
How To Recover From A Ransomware Attack
Ransomware attacks have doubled since the first half of the year and are targeting over 50% of organizations globally. But how does ransomware work, and how can you recover from an attack?

Ransomware is a type of cyberattack involving malware. Once downloaded to the user’s device, the malware holds corporate data hostage, locking users out or rendering it indecipherable through encryption, until the organization pays a ransom to restore it.
Cybercriminals are known to take advantage of uncertainty and change, and the global workplace has experienced huge changes in recent years; first, as the COVID-19 pandemic catalyzed the shift to remote work, and now, as many organizations welcome their employees back into the office in a hybrid working format. These employees are bringing devices with them that may have been connected to unsecured networks, used for personal purposes, or shared with partners over the last two years—all of which leave them vulnerable to malware exploits. And if any of those devices are infected, that threat can easily spread to other systems once the device is reconnected to the corporate network.
But that’s not the only risk organizations are currently facing. IoT devices are becoming increasingly popular in the workplace, as organizations welcome the use of smart devices, such as security cameras and coffee machines, that are designed to help us live and work more efficiently. But 2021 saw a global 33% increase in malware targeting IoT devices. Notoriously difficult to keep patched against vulnerability exploits, IoT devices can create a huge weakness within a company’s infrastructure when not properly managed—and when connected to the network without permission from the IT team, these vulnerabilities can easily go unnoticed.
The same study found that the number of ransomware attacks saw a global year-to-date increase of 148%, making 2021 the most dangerous and costly year for ransomware the company has ever recorded. And unfortunately, attack incidents aren’t only on the rise; they’re also becoming increasingly sophisticated. With bad actors constantly finding new ways to evade security layers, it’s inevitable that most companies will face a ransomware attack at some point.
But how do attackers find their way into your systems in the first place, and what can you do to recover from a ransomware attack?
What Is Ransomware And How Does It Work?
There are two main types of ransomware: crypto-ransomware and locker-ransomware. Crypto-ransomware encrypts an organization’s data and demands a ransom in order to have the files decrypted and safely returned. Locker-ransomware works in much the same way, except that it prevents users from accessing the files instead of encrypting them, before demanding a ransom for the data to be “unlocked”. In both cases, the attacker demands payment, threatening to publish sensitive information or permanently remove data from the system if the victim fails to pay up.
But how does ransomware get onto your system in the first place?
Well, it often starts with a trojan. A trojan is a type of malware that tricks victims into thinking it’s harmless by disguising itself as legitimate software. Emotet is a particularly infamous trojan that was first identified in 2014, and has recently reared its ugly head in a series of attacks that cause it to be one of the most prevalent ongoing threats that organizations are currently facing, according to a warning issued by the CISA.
Trojans like Emotet are primarily spread through spam mails. If the recipient opens the attached file or clicks on the URL, they unknowingly download the trojan, which then has the power to steal sensitive data. But attackers can also use it to spread other malware, like TrickBot or Qbot. This second layer of malware then spreads laterally through the company, stealing credentials, deploying backdoors and, perhaps most importantly, trying to access the domain controller. If they succeed in accessing the domain controller, the attacker can then deploy ransomware such as Ryuk, which encrypts the organization’s data and demands the ransom.
Some ransomware, however, doesn’t require user interaction to spread. Worms like WannaCry are a type of malware that replicate themselves so that they can tear through a system like wildfire, without the need for someone to keep passing it on via malicious URLs or attachments.
How Big Is The Threat Of Ransomware?
Ransomware attacks have increased dramatically in the last year, even more so in the last few months, but it’s important to understand what these figures mean for your organization. A recent report found that 51% of the 5000 organizations interviewed were hit by ransomware in the last year. Of these reported incidents, 73% of attackers succeeded in encrypting the victim organization’s data.
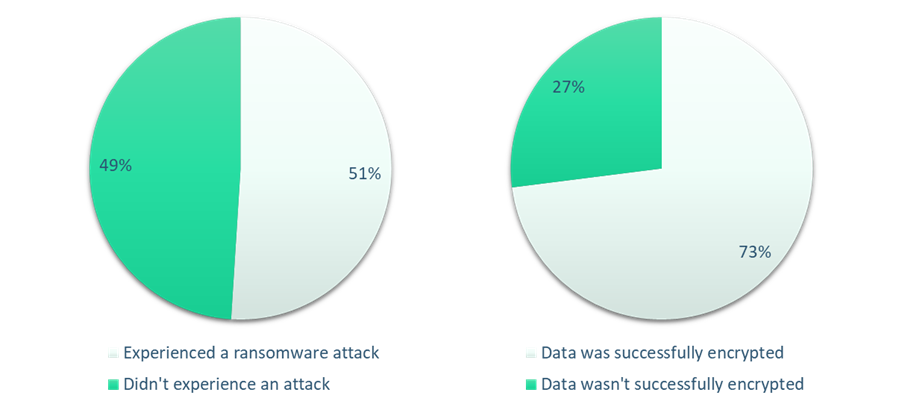
With the number of daily attacks globally increasing by up to 50% in the last quarter, that means that organizations are almost three times more likely to have fallen victim to an attack this year than to have evaded all attempts. It also means that half of organizations worldwide are likely to have experienced a successful attack in the last quarter.
So we know that the threat level is dauntingly high, but who is most at risk of facing ransomware attacks?
“Since every organization in our modern world relies on technology to keep operations running, every organization needs to protect themselves from ransomware attacks,” says Caroline Seymour, VP, Product Marketing of Zerto.
Headlines tend to feature high-profile attacks on large enterprises that end up costing the organizations billions to resolve. But we often don’t hear about the 46% of small businesses that are targeted by ransomware (2020 Data Breach Investigations Report, Verizon). SMBs are just as at risk as large corporations with a lot to lose, simply for the fact that they often don’t have the budget or infrastructure to invest in sophisticated security platforms and the latest technology updates. This makes them an easy target for cybercriminals looking for vulnerabilities to exploit, such as unpatched software. The notorious 2017 WannaCry ransomware attack spread in exactly this way: it targeted organizations that didn’t roll out the latest Windows patch. The UK’s National Health Service was one such victim.
“Just in the past year, [Zerto have] seen ransomware target large and small organizations, B2B and B2C companies, government organizations, and even organizations that are just trying to help people, like hospitals,” Seymour says. “Cybercriminals don’t discriminate; they will target any organization they think they can take advantage of.”
All of this means that your organization is likely to fall victim to a ransomware attack at some point. It could be next week or a few years down the line, and the attacker could demand hundreds of dollars or millions of dollars. Because of this, it’s crucial that you know how to react to a ransomware attack, and the steps that you need to take to recover from it.
How Can You Recover From A Ransomware Attack?
1. Don’t pay the ransom.
First things first: don’t pay the ransom. Unless you haven’t got any copies of your data stored elsewhere at all, in which case you need to weigh up the cost of the data loss vs the demanded payment. There are a few reasons for this:
- Remember that you’re dealing with a criminal, here. Paying the ransom doesn’t guarantee that you’ll actually get your data back.
- You’re proving that the attacker’s process works, which will encourage them to target further organizations who, in turn, will follow your example and pay up – it’s a vicious circle.
- Paying the ransom doubles the cost of dealing with an attack. If you do get your data back, the malware will still be on your servers, so you’ll still need to thoroughly cleanse them. You’ll also be paying for downtime, people time, device cost and so on, on top of the ransom.
Sophos’ survey found that 26% of ransomware victims had their data returned after paying the ransom, and 1% paid the ransom but didn’t get their data back. 56% of victims, more than twice as many as those who paid the ransom, recovered their data through backups – we’ll come back to this.
2. Report the attack.
Once you’ve taken a deep breath and put away your wallet, you need to report the attack. This will help authorities identify the attacker and how they’re choosing their targets, and help prevent other organizations from falling victim to the same attack.
Generally, you can contact your local police, who will put you through to their cybercrime investigations department. If in the US, you can also report via the On Guard Online website; in the UK, through Action Fraud.
3. Cleanse your systems.
There are some software packages available that claim to be able to eradicate ransomware from your systems, but there are two problems with this. The first is that you can’t be sure that anyone other than the attacker will be able to completely remove the ransomware. The second is that, even if your system is successfully cleansed, you still may not be able to access your data. Unfortunately, there isn’t a decryption tool for every type of ransomware out there, and the newer and more sophisticated the ransomware, the more time it will take experts to develop a tool to unscramble your files.
On top of that, encryption involves running a decryption key and the original file through a function together to recover the original file. However, modern attacks use a unique key for each victim, so it could take years for even a powerful supercomputer to find the right key for an individual victim. TeslaCrypt is a good example of this: the original ransomware only needed a single key to unlock multiple victims’ data, but modern variants of the attack allow the criminal to use unique encryption keys for each victim.
Because of this, the best plan of action is to completely wipe all of your storage devices and start afresh, reinstalling everything from the bottom up. This will make sure that there aren’t any traces of ransomware lurking in dark corners, and you’ll have a clean slate on which to restore your data.
4. Restore your data.
This is where we come back to the backups. Data backup is traditionally considered an IT compliance issue, carried out to tick boxes and get through audits. However, it’s becoming increasingly viewed as a security topic, and for good reason.
“Preventing a cyberattack isn’t always possible, but mitigating the impact certainly is, which is why backup should be considered a security issue,” Seymour explains. “Once an organization becomes a ransomware victim, it’s faced with a dilemma: pay the ransom, which is never advised, or move forward without the data. If the organization has a proper backup strategy in place to counteract cyberattacks, it can quickly recover by accessing its backed up data and avoid costly downtime.”
There are a few ways to restore your data through backups. The first is by carrying out a DIY system restore. Pros: it’s fairly cheap and easy to do. Cons: There could be traces of malware buried in the data you’re trying to restore, and you won’t be able to recover any personal files. That means that this route could take you back to step one and, even if it doesn’t, you won’t have access to everything that you lost. This is why you should always make sure that you have a strong backup solution in place so that you can use the second restoration method: third-party disaster recovery.
Backup and recovery solutions capture a point-in-time copy of all of your files, databases and computers and write those copies out to a secondary storage device isolated from your local computers. The pros here include assured and secure recovery of all of your files and external support from the vendor so that you don’t have to manage the recovery alone. The only con is that you have to pay for the solution – you can’t have everything, I suppose.
The best backup and recovery solutions designed to help organizations recover from ransomware attacks feature point-in-time recovery, also known as continuous data protection or journaling. This exceptionally tight version-controlled method of recovery allows organizations to recover data from up to seconds before the ransomware hit.
“With a backup strategy that includes continuous data protection (CDP), organizations can be sure their data is always available and always secure,” says Seymour. “CDP allows organizations to fully recover their data with the granularity to go back to a specific point in time precisely before the attack occurred, minimizing any data loss.” According to Caroline, the best CDP solutions are flexible enough to recover exactly what the organization needs, whether that’s a few files, virtual machines, or a complete application stack. “This assures a fast return to a functioning state,” she explains. “Traditional backup tools based on snapshots put an organization at risk for data loss between snapshots.”
How Can You Prevent A Repeat Ransomware Attack?
Hack me once, shame on you. Hack me twice… Well, we don’t want that happening, so it’s important that you put measures in place to help prevent ransomware gaining access to your systems a second time. Here are some of the best protections that you can use stop ransomware attacks:
Endpoint Detection And Response
Once you’ve recovered from a breach, you need to make sure that it won’t happen again. Cleansing your system of malicious files isn’t enough – you need to identify what caused the breach in the first place and work out what the attacker did before they managed to encrypt or lock down your data.
Endpoint detection and response (EDR) solutions continuously monitor all incoming and outgoing traffic on a network for potential threats. If a threat is detected, the solution isolates the affected machine so that the malware can’t spread. But here’s the important part: EDR doesn’t just keep a record of the incident itself, but of all the events that led up to the incident, too. This means that you can see which files, processes and registry keys the hacker accessed, and identify where the attack started and how it progressed. You can then use this information to stop the same incident from occurring again.
Antivirus Software
Antivirus software secures individual endpoints by detecting and blocking malicious files, and warning users when they’re visiting suspicious websites. Today, most endpoint protection software is hosted in the cloud, which means that solutions can use advanced machine learning technology to automate analytics and improve detection rates.
Email Security
Secure Email Gateways (SEGs) filter incoming and outgoing email communications to identify threats and prevent them from being delivered. This can stop ransomware from ever reaching its intended victim.
However, cybercriminals are always looking for new ways in, so their attacks are becoming increasingly sophisticated – particularly when it comes to phishing. SEG’s can block phishing attacks, but may let some highly targeted or personalized communications slip through. If this happens, a Post-Delivery Protection solution can detect it, using powerful AI algorithms and stylometry to detect advanced attacks and alert users by inserting a warning banner into high-risk emails.
Web Filtering Technology
There are two main types of web filtering: cloud-based and DNS. Both of them protect users from accessing malicious websites, such as phishing pages, and from downloading content from these websites. Cloud web filtering platforms filter harmful websites by scanning for malicious code and filtering harmful URLs. They also block web-based malware from being downloaded to the user’s device. DNS (domain name system) web filtering platforms are a type of cloud-based filter that sort internet traffic based on DNS lookups. All websites have a unique IP address that browsers connect to the domain name to be able to load the page. DNS filters sit between the browser and domain so that the browser can’t load any malicious sites.
Phishing Awareness Training
Unfortunately, employees are often an organization’s biggest security risk, simply because they aren’t aware of the dangers they’re facing every day. Cybercriminals exploit this lack of awareness by impersonating a trustworthy source so that unsuspecting users won’t question them when they ask for sensitive information or send them an unusual file to download. Education is one of the best defenses against social engineering attacks, and strong phishing awareness training solutions can transform your employees into a powerful line of defense. The best solutions even allow you to send simulated phishing emails to your workforce, testing their resilience and showing you where you could improve.
Summary
Chances are, you’re going to face a ransomware attack at some point. The key is in making sure you know what to do when it happens, and being able to restore your data securely once your system is cleansed of all traces of the malware.
Of course, to be able to restore your data, you need to have copies of your files stored safely elsewhere. The “3 2 1” best practice recommends that you keep three copies of your data in two separate locations, and at least one of the copies should be stored in a different medium to the others, e.g. in object storage, cloud-based storage or on a disk. The most secure way of doing this is by investing in a third-party disaster recovery solution. There are a lot of these available, each with slightly different feature sets, so it’s important that you choose the product that best meets your business need. We’ve put together a list of the best backup and recovery solutions currently on the market to help you get started.



